When a VM is connected to a Nutanix managed network, when is the IP addressed assigned?
Correct Answer:
B
When a VM is connected to a Nutanix managed network, the IP address is assigned when the VM is powered on. A Nutanix managed network is a network that is created and managed by Prism Central using IP address management (IPAM). IPAM allows Prism Central to automatically assign IP addresses to VMs from a pool of available addresses in a subnet. IPAM also tracks the IP address usage and availability across clusters and networks4.
When a VM is connected to a Nutanix managed network, the administrator can choose one of the following assignment types for the IP address:
✑ Assign Static IP: This option allows the administrator to manually specify a static
IP address for the VM from the subnet range. The IP address will not change unless the administrator changes it.
✑ Assign with DHCP: This option allows Prism Central to dynamically assign an IP
address for the VM from the subnet range using DHCP. The IP address may change depending on the DHCP lease time and availability.
✑ No Private IP: This option allows the administrator to skip assigning an IP address
for the VM. This option is useful for scenarios where the administrator wants to use an external IPAM solution or assign an IP address later5.
Regardless of the assignment type, the IP address is assigned when the VM is powered on. This is because Prism Central needs to communicate with the hypervisor (AHV or ESXi) to configure the virtual NIC (vNIC) of the VM with the IP address information. This communication can only happen when the VM is in a powered on state6.
References: 4: IP Address Management - Prism Central Guide 5: Creating a New Report - Prism Central Guide 6: IP Address Assignment - AHV Networking Guide
Refer to the exhibit.
Which two initial cluster configuration tasks were missed during the deployment process? (Choose two.)
Correct Answer:
AD
According to the image description, the exhibit shows a screenshot of a computer screen with a table of data. The table has 6 columns and 4 rows. The columns are labeled ??Date??, ??Time??, ??Status??, ??Details??, ??Configuration??, and ??Duration??. The rows contain information about different configurations and their statuses. The background is a light blue color. There is a pop-up message on the bottom right corner of the screen that reads ??This question has been answered. Click here to enable the edit button.??
Based on the table data, it seems that the screenshot is taken from the Prism Central web console, showing the results of a cluster health check report. The report shows that there are four failed checks: Host Password Policy, CVM Password Policy, NTP Configuration, and Cluster Time Skew2. These checks indicate that some initial cluster configuration tasks were missed during the deployment process.
The Host Password Policy check verifies that the host passwords are not set to default values and are compliant with the password policy defined in Prism Central3. The CVM Password Policy check verifies that the CVM passwords are not set to default values and are compliant with the password policy defined in Prism Central4. These checks are important for ensuring the security and compliance of the cluster. Therefore, changing the host and CVM passwords from their default values and following the password policy guidelines are two initial cluster configuration tasks that were missed.
References: 1: VM Details View - Nutanix Support & Insights 2: Cluster Health - Nutanix Support & Insights 3: Host Password Policy - Nutanix Support & Insights 4: CVM Password Policy - Nutanix Support & Insights
An administrator needs to run a mixed Exchange and SQL workload with a guaranteed amount of container space for each application.
How should the administrator meet this requirement?
Correct Answer:
D
Reference: https://portal.nutanix.com/page/documents/details?targetId=Web_Console_Guide-
NOS_v4_0:wc_security_authentication_wc_t.html
Which scenario would benefit most from Erasure Coding being enabled on a container?
Correct Answer:
A
The correct answer is A. Long term storage of data which is written once and read infrequently.
Erasure Coding is a feature that increases the usable capacity on a Nutanix cluster by reducing the amount of data replication. Instead of replicating data, Erasure Coding uses parity information to rebuild data in the event of a disk failure. The capacity savings of Erasure Coding is in addition to deduplication and compression savings1.
Erasure Coding is most beneficial for scenarios where the data is written once and read infrequently, such as long term storage of archival data, backup data, or cold data. This is because Erasure Coding has some trade-offs and limitations that may affect the performance and availability of the cluster. Some of these trade-offs and limitations are2:
✑ Erasure Coding requires more CPU and memory resources than replication, as it
involves more complex calculations for encoding and decoding data.
✑ Erasure Coding increases the network bandwidth consumption, as it involves more data transfers between nodes for encoding and decoding data.
✑ Erasure Coding reduces the resiliency of the cluster, as it can tolerate fewer node failures than replication. For example, a cluster with redundancy factor 2 can tolerate one node failure with replication, but only two disk failures with Erasure Coding.
✑ Erasure Coding is not effective for workloads that have many overwrites or random writes, as it involves more overhead for updating the parity information.
✑ Erasure Coding is not supported for some features, such as volume groups, file
server VMs, or Metro Availability.
Therefore, if an administrator needs to configure a container on a Nutanix cluster, they should enable Erasure Coding only if the container will store data that is written once and read infrequently. This way, they can maximize the capacity savings of Erasure Coding without compromising the performance and availability of the cluster.
Reference: Erasure Coding | Nutanix Community
Refer to Exhibit: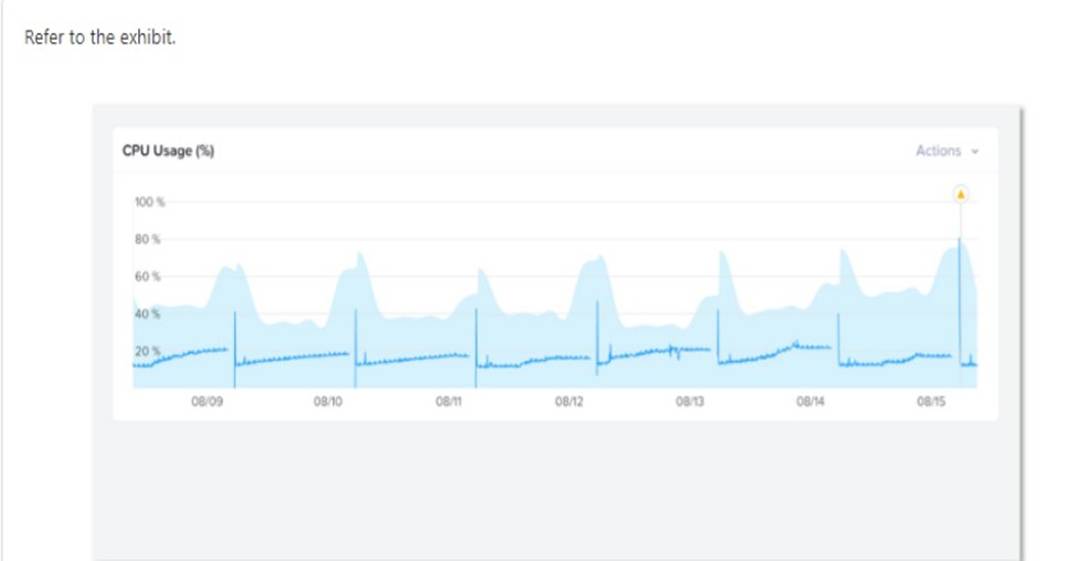
Why has an anomaly been triggered?
Correct Answer:
A
Nutanix leverages a method for determining the bands called ??Generalized Extreme Studentized Deviate Test??. A simple way to think about this is similar to a confidence interval where the values are between the lower and upper limits established by the algorithm.
Another web source3 shows an example of how anomaly detection works in Nutanix Prism Central. In the video, you can see that when the observed value of a metric deviates significantly from the predicted value based on historical data, an anomaly event is triggered and displayed on a chart.
Therefore, by comparing the observed values with the predicted values based on historical data, Nutanix anomaly detection can identify abnormal behavior and alert you accordingly.

