A cloud engineer is reviewing the following Dockerfile to deploy a Python web application: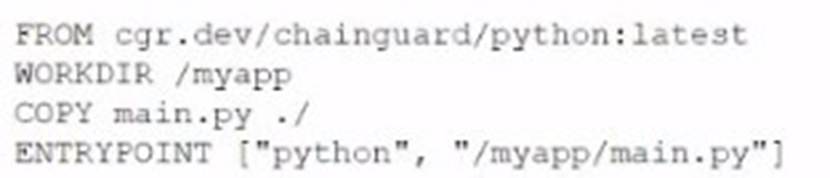
Which of the following changes should the engineer make lo the file to improve container security?
Correct Answer:
A
To improve container security, the engineer should add the instruction "USER nonroot" to the Dockerfile. This change ensures that the container does not run as the root user, which reduces the risk of privilege escalation attacks. Running containers as a non-root user is a best practice for enhancing security in containerized environments.References: CompTIA Cloud+ content includes security concerns, measures, and concepts for cloud operations, highlighting container security best practices such as running containers with least privilege to mitigate security risks.
An organization wants to ensure its data is protected in the event of a natural disaster. To support this effort, the company has rented a colocation space in another part of the country. Which of the following disaster recovery practices can be used to best protect the data?
Correct Answer:
D
For an organization looking to protect its data in the event of a natural disaster, the best disaster recovery practice would be off-site replication. By renting a colocation space in another part of the country, the company can maintain copies of their data and critical systems in a geographically separate location, ensuring they are not affected by the same disaster. References: CompTIA Cloud+ Study Guide (Exam CV0-004) - Chapter on Disaster Recovery
Department supervisors have requested a report that will help them understand the utilization of cloud resources, make decisions about budgeting for the following year, and reduce costs. Which of the following are the most important requisite steps to create the report? (Select two).
Correct Answer:
DE
To create a report that helps understand the utilization of cloud resources, make budget decisions, and reduce costs, the most important steps are to enable resource tagging and configure the collection of performance/utilization logs. Resource tagging helps in categorizing and tracking costs by associating tags with resources, while performance/utilization logs are essential for analyzing resource usage over time. References: CompTIA Cloud+ Study Guide (Exam CV0-004) - Chapter on Cloud Management
A cloud infrastructure administrator updated the IP tables to block incoming connections and outgoing responses to 104.225.110.203. Which of the following vulnerability
management steps is this an example of?
Correct Answer:
B
Updating the IP tables to block connections to a specific IP address as a response to vulnerabilities is an example of remediation. Remediation involves taking direct action to fixvulnerabilities, such as by applying patches, changing configurations, or, in this case, updating firewall rules to block potentially harmful traffic.
References: CompTIA Cloud+ resources and vulnerability management processes
A cloud engineer is designing a high-performance computing cluster for proprietary software. The software requires low network latency and high throughput between cluster nodes.
Which of the following would have the greatest impact on latency and throughput when designing the HPC infrastructure?
Correct Answer:
A
Node placement is critical in high-performance computing (HPC) clusters where low network latency and high throughput are required. Proper placement of nodes within the network infrastructure, including proximity to each other and to key network components, can significantly reduce latency and increase throughput. Ensuring that nodes are physically close and well-connected can facilitate faster data transfer rates between them. References: CompTIA Cloud+ Certification Study Guide (Exam CV0-004) by Scott Wilson and Eric Vanderburg

