A company's website suddenly crashed. A cloud engineer investigates the following logs: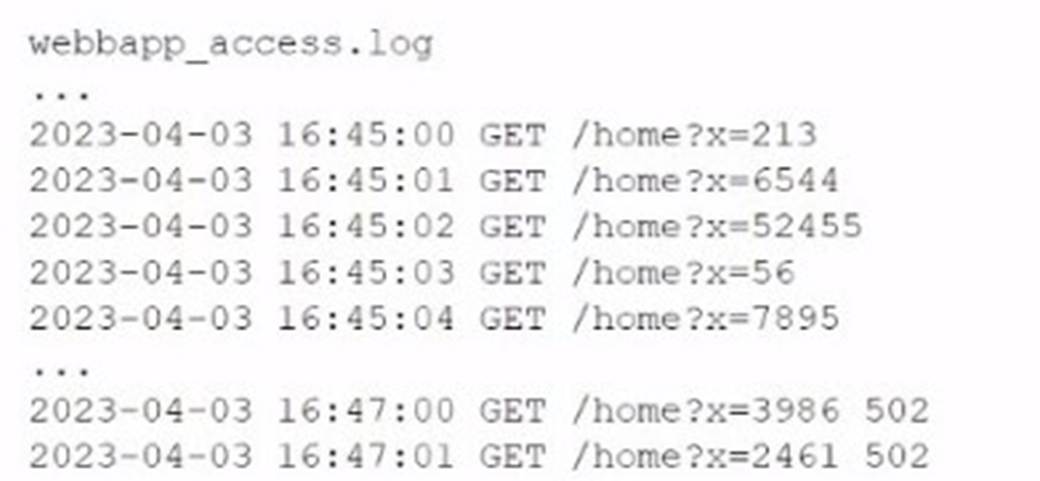
Which of the following is the most likely cause of the issue?
Correct Answer:
D
The logs indicate a sudden surge in access requests to the website's homepage, followed by 502 errors, which are indicative of server overload or failure to handle incoming requests. This pattern is typical of a Distributed Denial of Service (DDoS) attack, where multiple compromised systems flood the target with traffic, exceeding its capacity to handle requests, leading to service disruption.
An organization's web application experiences penodic bursts of traffic when a new video is launched. Users are reporting poor performance in the middle of the month. Which of the following scaling approaches should the organization use to scale based on forecasted traffic?
Correct Answer:
A
For periodic bursts of traffic that are predictable, such as when a new video is launched, a scheduled scaling approach is suitable. This strategy involves scaling resources based on forecasted or known traffic patterns, ensuring that the infrastructure can handle the load during expected peak times.References: The use of scheduled scaling to manage predictable traffic increases is discussed within the Management and Technical Operations section of the CompTIA Cloud+ exam objectives.
SIMULATION
A company has decided to scale its e-commerce application from its corporate datacenter to a commercial cloud provider to meet an anticipated increase in demand during an upcoming holiday.
The majority of the application load takes place on the application server under normal conditions. For this reason, the company decides to deploy additional application servers into a commercial cloud provider using the on-premises orchestration engine that installs and configures common software and network configurations.
The remote computing environment is connected to the on-premises datacenter via a site- to-site IPSec tunnel. The external DNS provider has been configured to use weighted round-robin routing to load balance connections from the Internet.
During testing, the company discovers that only 20% of connections completed successfully.
INSTRUCTIONS
Review the network architecture and supporting documents and fulfill these requirements: Part 1: Analyze the configuration of the following components: DNS, Firewall 1, Firewall 2, Router 1, Router 2, VPN and Orchestrator Server.
Analyze the configuration of the following components: DNS, Firewall 1, Firewall 2, Router 1, Router 2, VPN and Orchestrator Server. Identify the problematic device(s).
Identify the problematic device(s).
Part 2: Identify the correct options to provide adequate configuration for hybrid cloud architecture.
Identify the correct options to provide adequate configuration for hybrid cloud architecture.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Part 1:
Cloud Hybrid Network Diagram
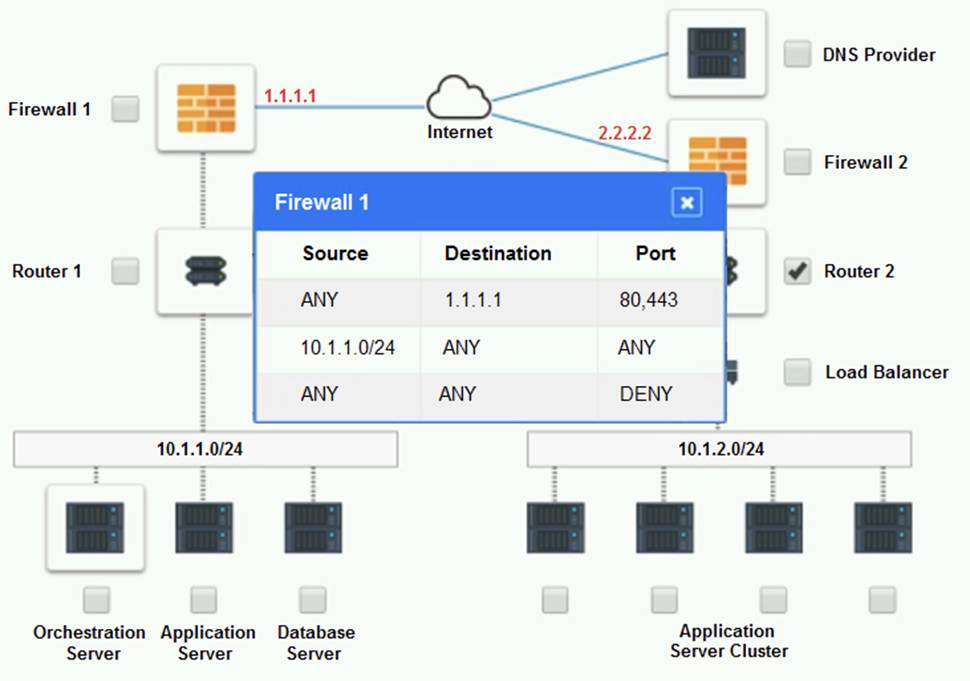
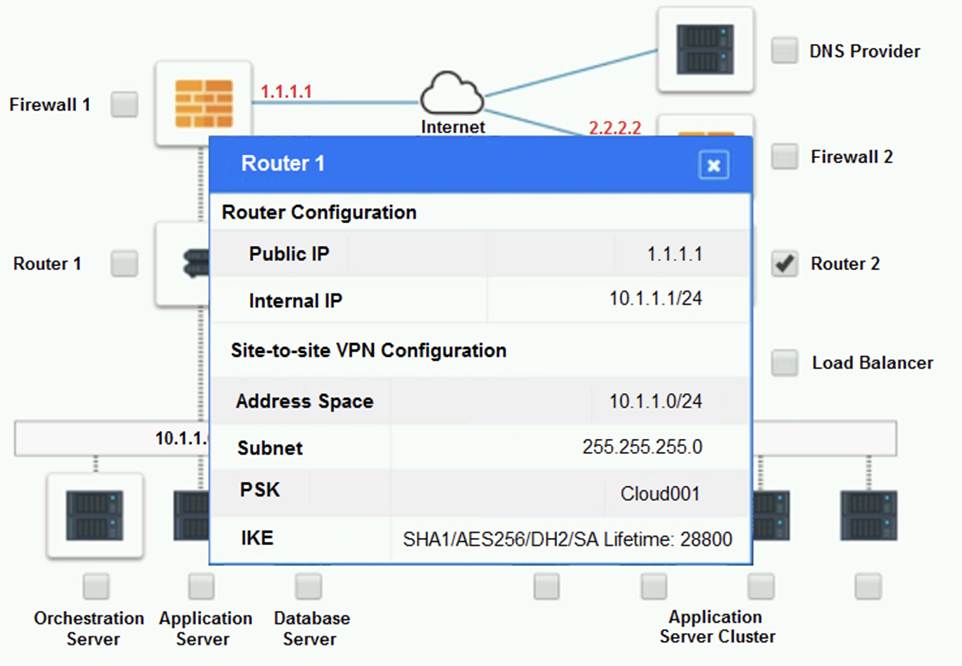
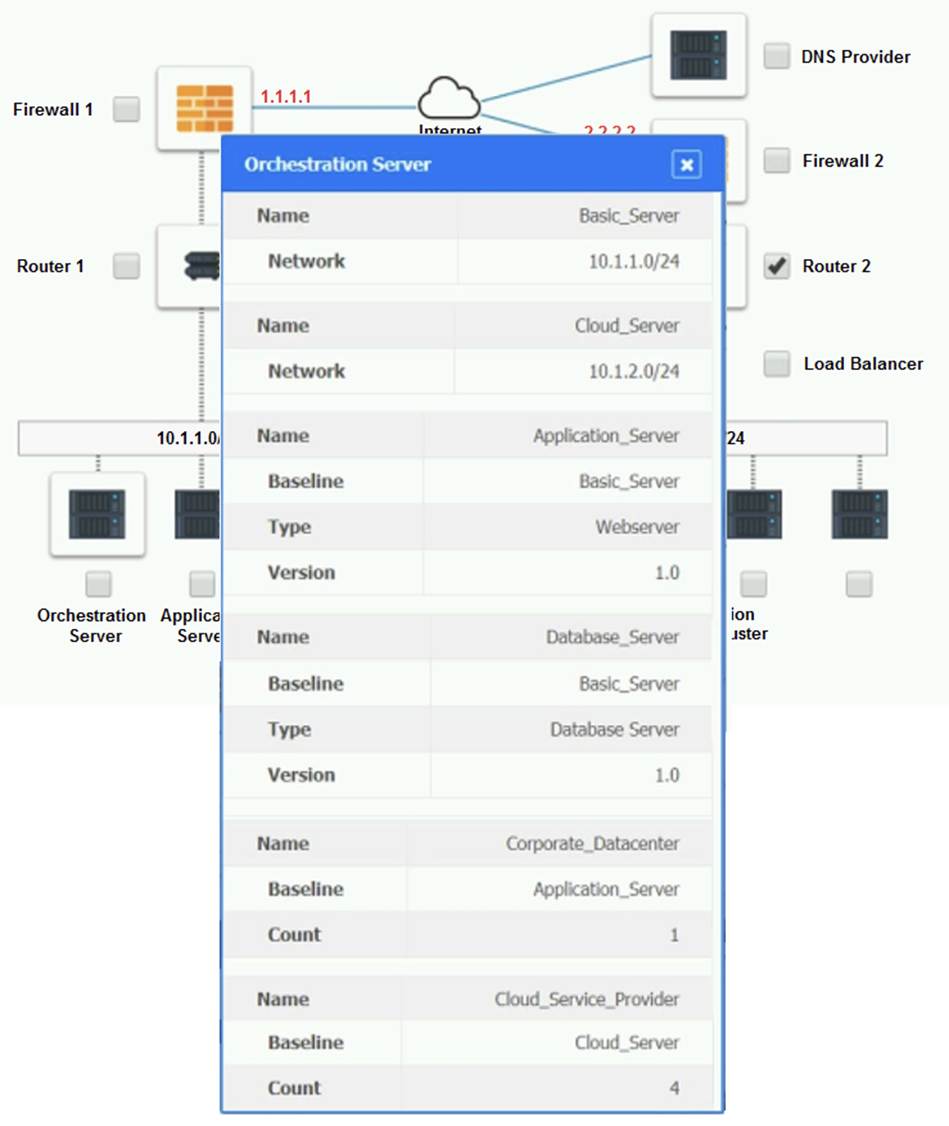
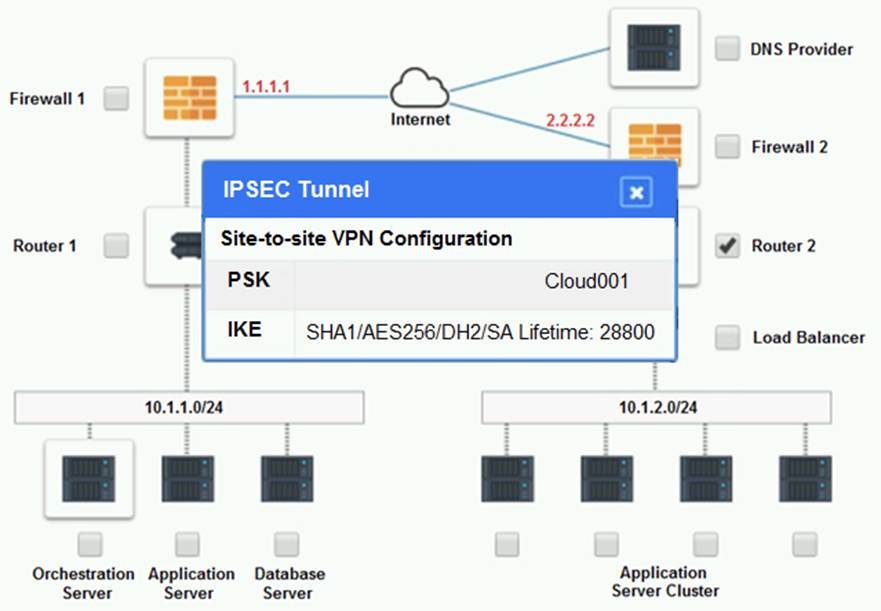
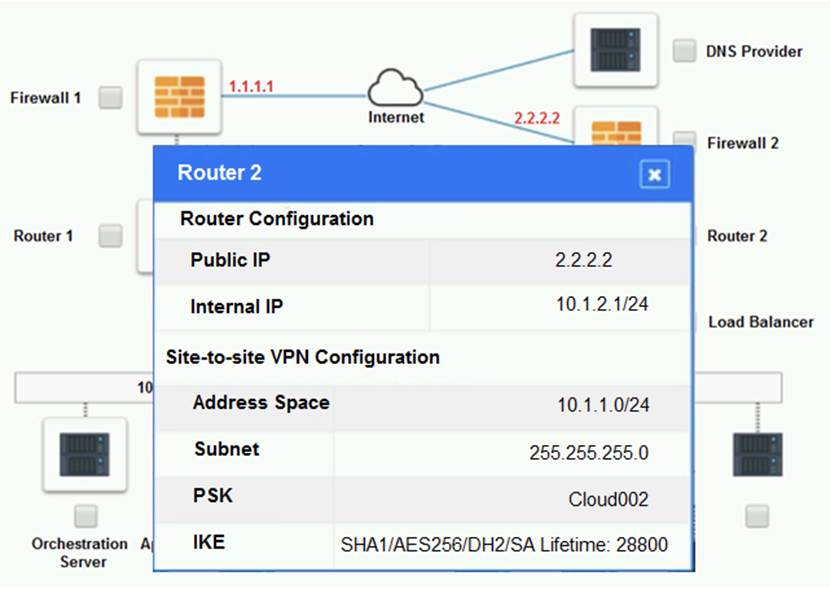
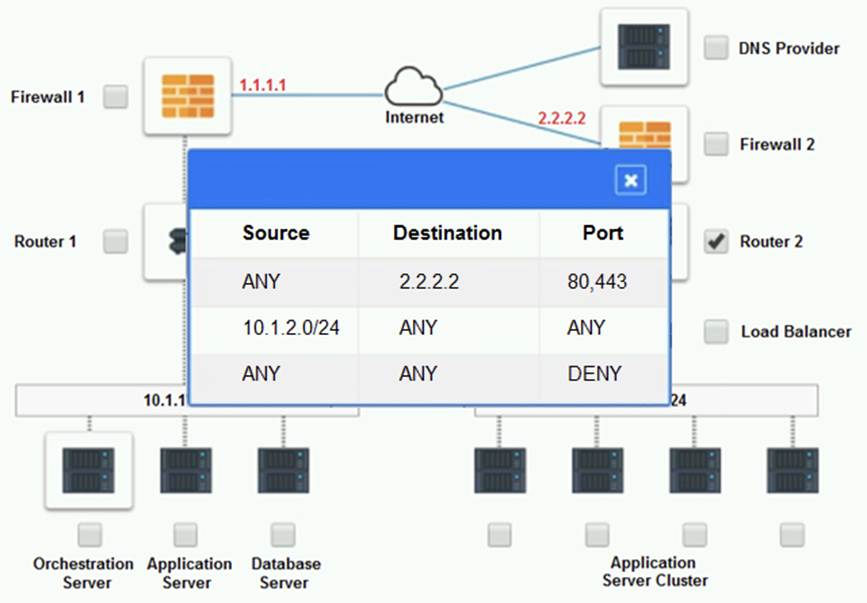
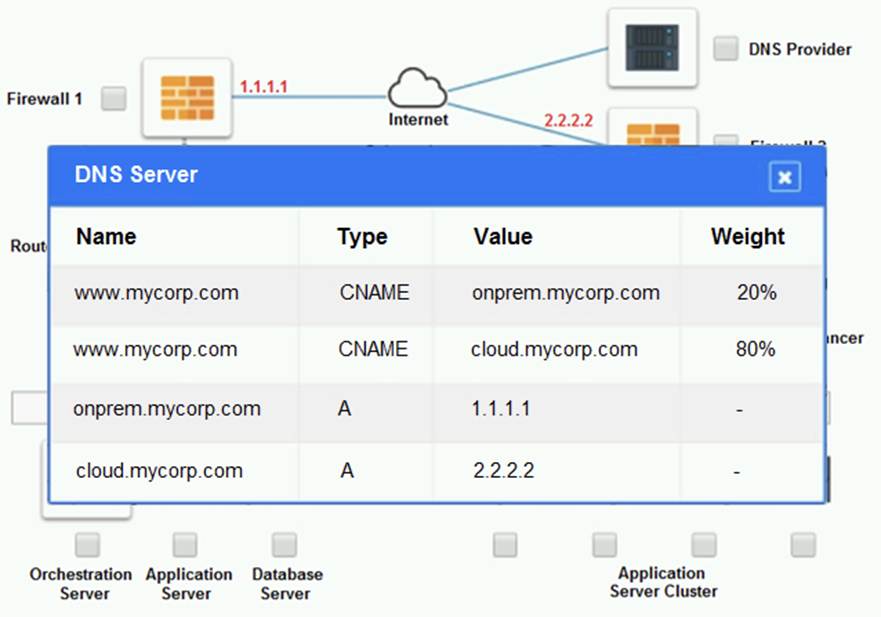
Part 2:
Only select a maximum of TWO options from the multiple choice question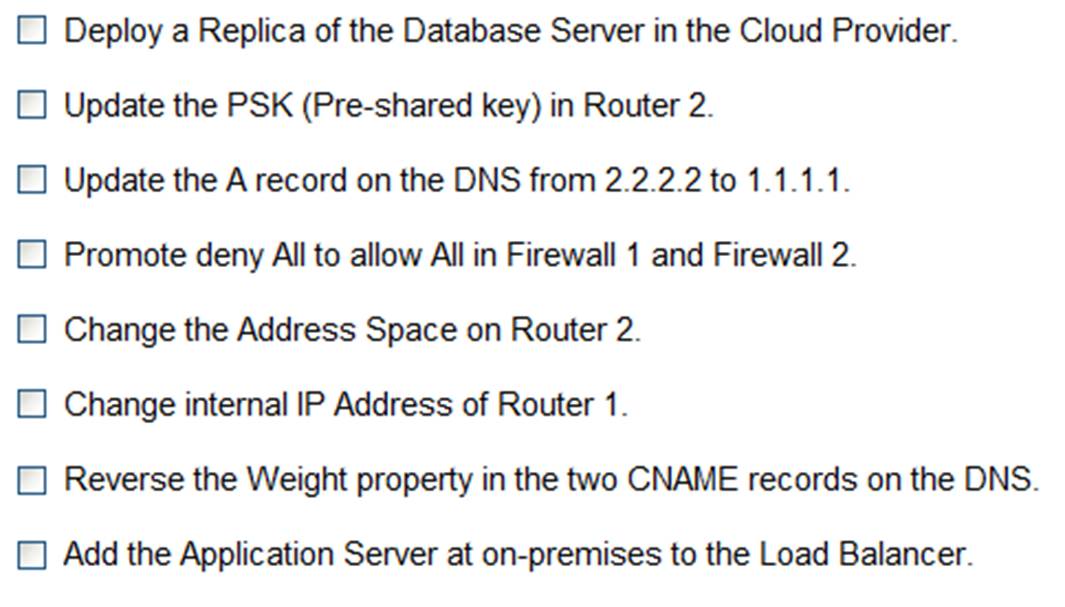
Solution:
Part 1: Router 2
The problematic device is Router 2, which has an incorrect configuration for the IPSec tunnel. The IPSec tunnel is a secure connection between the on-premises datacenter and the cloud provider, which allows the traffic to flow between the two networks. The IPSec tunnel requires both endpoints to have matching parameters, such as the IP addresses, the pre-shared key (PSK), the encryption and authentication algorithms, and the security associations (SAs) .
According to the network diagram and the configuration files, Router 2 has a different PSK and a different address space than Router 1. Router 2 has a PSK of ??1234567890??, while Router 1 has a PSK of ??0987654321??. Router 2 has an address space of 10.0.0.0/8, while Router 1 has an address space of 192.168.0.0/16. These mismatches prevent the IPSec tunnel from establishing and encrypting the traffic between the two networks.
The other devices do not have any obvious errors in their configuration. The DNS provider has two CNAME records that point to the application servers in the cloud provider, with different weights to balance the load. The firewall rules allow the traffic from and to the application servers on port 80 and port 443, as well as the traffic from and to the VPN server on port 500 and port 4500. The orchestration server has a script that installs and configures the application servers in the cloud provider, using the DHCP server to assign IP addresses.
Part 2:
The correct options to provide adequate configuration for hybrid cloud architecture are:
✑ Update the PSK in Router 2.
✑ Change the address space on Router 2.
These options will fix the IPSec tunnel configuration and allow the traffic to flow between the on-premises datacenter and the cloud provider. The PSK should match the one on Router 1, which is ??0987654321??. The address space should also match the one on Router 1, which is 192.168.0.0/16.
* B. Update the PSK (Pre-shared key in Router2)
* E. Change the Address Space on Router2
Does this meet the goal?
Correct Answer:
A
A company wants to optimize cloud resources and lower the overhead caused by managing multiple operating systems. Which of the following compute resources would be best to help to achieve this goal?
Correct Answer:
B
Containers are the best compute resources to optimize cloud resources and lower the overhead caused by managing multiple operating systems. Containers encapsulate applications and their dependencies into a single executable package, running on a shared OS kernel, which reduces the need for separate operating systems for each application and simplifies resource management.References: CompTIA Cloud+ materials discuss management and technical operations in cloud environments, including the use of containers to improve resource utilization and operational efficiency by minimizing the overhead associated with traditional VMs.
A bank informs an administrator that changes must be made to backups for long-term reporting purposes. Which of the following is the most important change the administrator
should make to satisfy these requirements?
Correct Answer:
C
For long-term reporting purposes, the most critical aspect to consider is the retention period of the backups. This is because the bank will likely require access to historical data for audit, compliance, and reporting purposes. The retention policy will need to ensure that backups are kept for the required duration, which may be several years depending on regulatory and business needs. Adjusting the retention policy will help ensure that the necessary data is preserved for as long as it is needed, without unnecessary data accumulation that could lead to higher costs and management complexity.References: CompTIA Cloud+ Certification Study Guide (Exam CV0-004) by Scott Wilson and Eric Vanderburg

