A technician is setting up a Windows server to allow remote desktop connections for multiple users. Which of the following should the technician configure on the workstation?
Correct Answer:
A
Comprehensive and Detailed Explanation From Exact Extract:
To allow Remote Desktop Protocol (RDP) access, the firewall must be configured to allow inbound connections on TCP port 3389. If the Windows Firewall blocks RDP, users will not be able to connect remotely even if the feature is enabled in system settings.
* B. Computer Management allows configuration of services and local users, but not network access.
* C. User Accounts is for account setup and control, but enabling remote access requires firewall configuration.
* D. Ease of Access is unrelated to remote connectivity—it??s for accessibility features. Reference:
CompTIA A+ 220-1102 Objective 2.2: Compare and contrast security measures and firewall settings.
Study Guide Section: Enabling and securing RDP via firewall settings
===========================
A technician needs to install an operating system on a large number of workstations. Which of the following is the fastest method?
Correct Answer:
D
Comprehensive and Detailed Explanation From Exact Extract:
Image deployment is the fastest and most efficient method for installing operating systems on multiple machines. It involves creating a pre-configured image of an OS and deploying it across systems using tools like Windows Deployment Services (WDS) or third-party imaging solutions. This method saves time and ensures consistency across all devices.
* A. Physical media is slow and not scalable.
* B. Mountable ISOs are useful but still require manual installation.
* C. Manual installation is time-consuming and not suitable for large-scale deployment. Reference:
CompTIA A+ 220-1102 Objective 1.4: Given a scenario, use appropriate Microsoft operating system installation methods.
Study Guide Section: Deployment methods — image deployment, automation
SIMULATION
Multiple users are reporting audio issues as well as performance issues after downloading unauthorized software. You have been dispatched to identify and resolve any issues on the network using best practice procedures.
INSTRUCTIONS
Quarantine and configure the appropriate device(s) so that the users?? audio issues are resolved using best practice procedures.
Multiple devices may be selected for quarantine. Click on a host or server to configure services.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.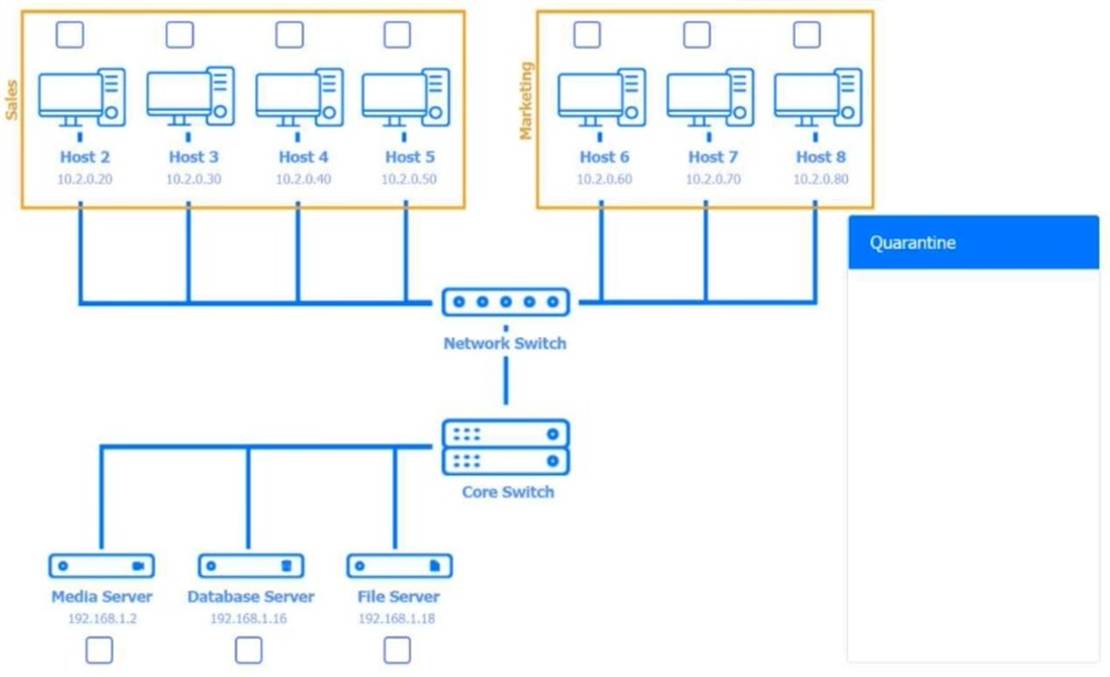
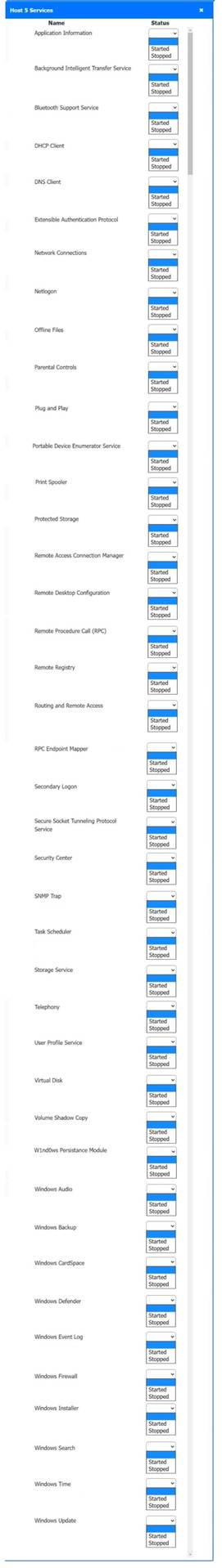
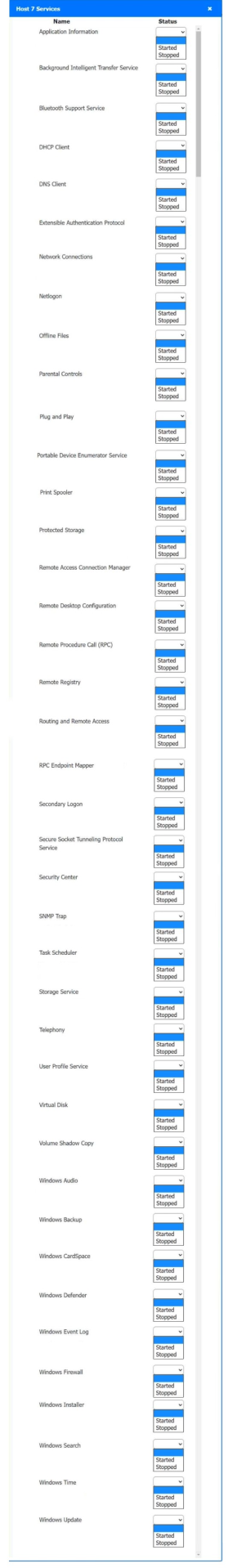
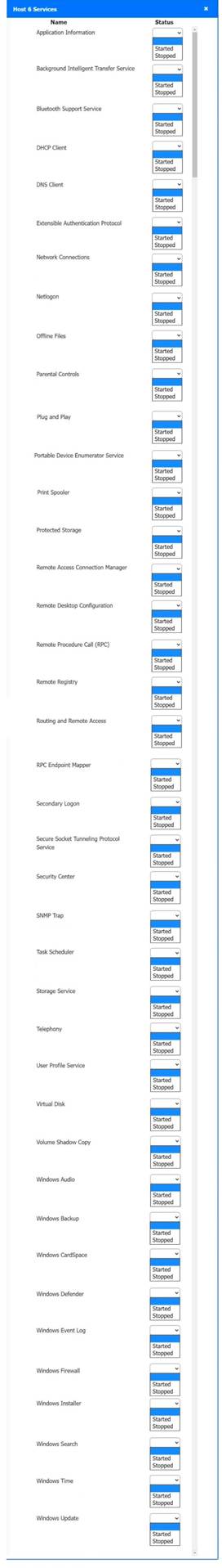

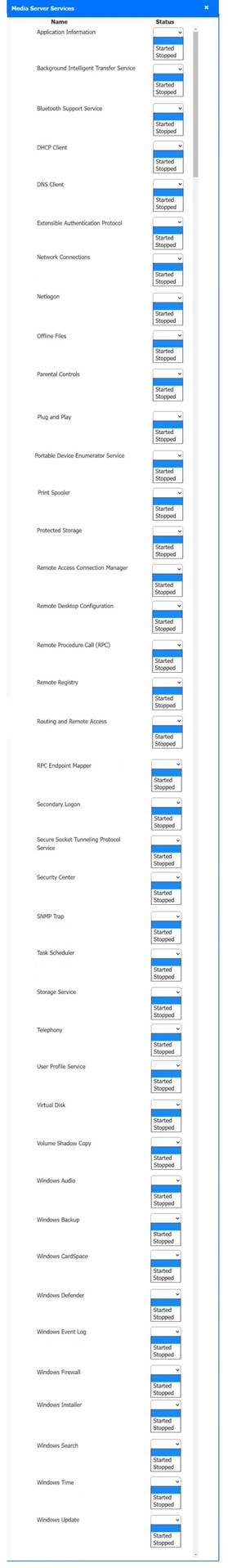
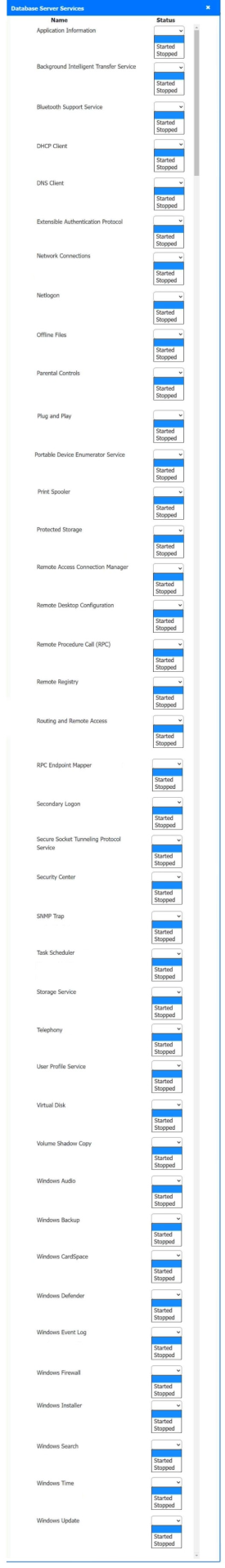
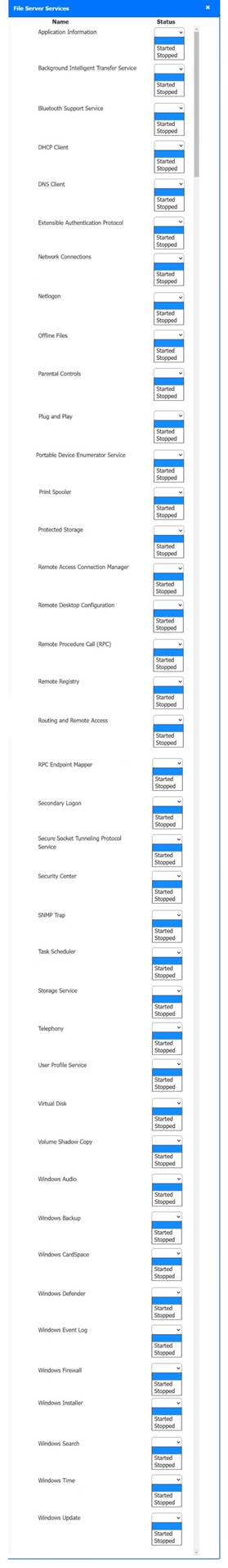
Solution:
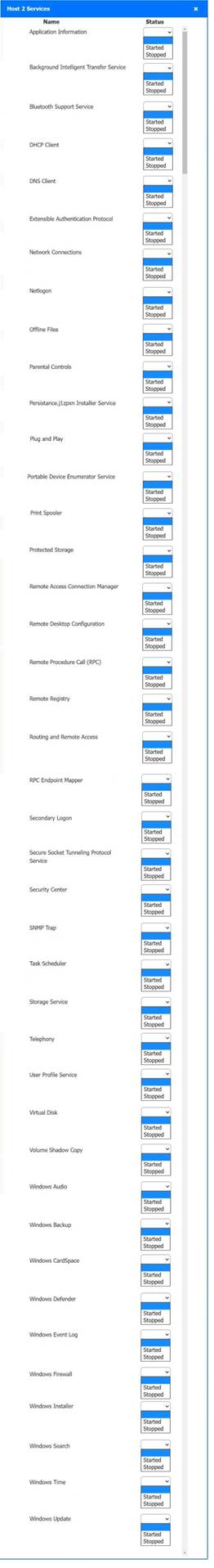
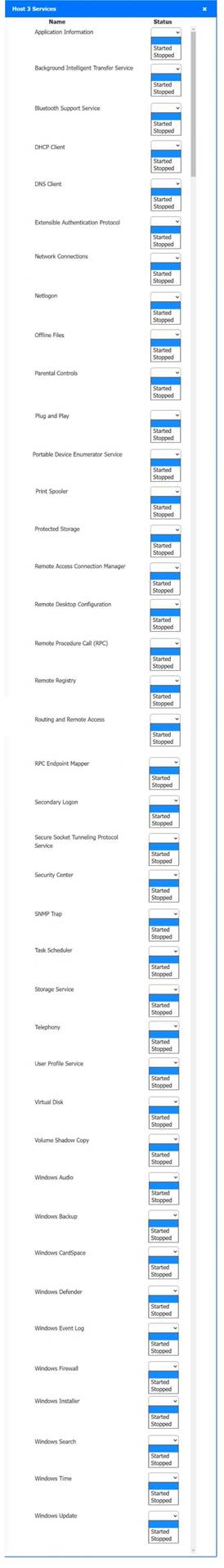
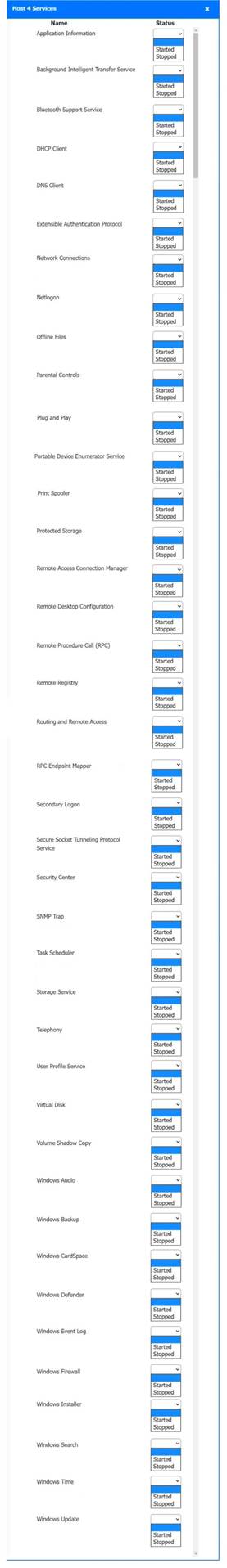
Host 2, Host 3, Host 4 , Host 5 ,Host 6, Host 7, Host 8 , Media Server - Stop All unwanted and malicious service (Persistance.j1zpxn Installer Service) from all the listed host and Media servers
Refer screenshot below on the required service started/stopped on host2, same service to be started and stopped across all host servers.
Does this meet the goal?
Correct Answer:
A
An administrator received an email stating that the OS they are currently supporting will no longer be issued security updates and patches. Which of the following is most likely the reason the administrator received this message?
Correct Answer:
B
Comprehensive and Detailed Explanation From Exact Extract:
Operating systems periodically reach a status known as "end of life" (EOL), at which point the developer (e.g., Microsoft, Apple) ceases to provide security updates, patches, or technical support. When this happens, the OS becomes vulnerable and non-compliant with security best practices, which is why organizations typically receive advance notifications from vendors or support teams.
* A. Manufacturer support expiration only applies to hardware, not OS patching.
* C. Security software may be upgraded or removed, but that does not affect patching the OS itself.
* D. The release of a new version doesn??t automatically stop updates for the current version. Reference:
CompTIA A+ 220-1102 Objective 1.3: Given a scenario, use appropriate Microsoft operating system features and tools.
Study Guide Section: OS lifecycle management and vendor support phases (e.g., EOL)
===========================
A technician needs to configure laptops so that only administrators can enable virtualization technology if needed. Which of the following should the technician configure?
Correct Answer:
A
Comprehensive and Detailed Explanation From Exact Extract:
Virtualization settings are typically found within the BIOS/UEFI firmware configuration. To prevent unauthorized users from changing these settings, the technician should set a BIOS password. This ensures only administrators with the password can access or modify BIOS settings, including virtualization support.
* B. The guest account is a user-level feature in Windows and doesn??t control BIOS access.
* C. A screen lock prevents casual access to the desktop but doesn??t protect firmware settings.
* D. AutoRun controls how media and devices behave when inserted — unrelated to BIOS security.
Reference:
CompTIA A+ 220-1102 Objective 2.2: Compare and contrast security measures and administrative controls.
Study Guide Section: BIOS/UEFI settings protection — password implementation

