During a gap assessment, an organization notes that OYOD usage is a significant risk. The organization implemented administrative policies prohibiting BYOD usage However, the organization has not implemented technical controls to prevent the unauthorized use of BYOD assets when accessing the organization's resources. Which of the following
solutions should the organization implement to b»« reduce the risk of OYOD devices? (Select two).
Correct Answer:
BC
To reduce the risk of unauthorized BYOD (Bring Your Own Device) usage, the organization should implement Conditional Access and Network Access Control (NAC). Why Conditional Access and NAC?
✑ Conditional Access:
✑ Network Access Control (NAC):
Other options, while useful, do not address the specific need to control and secure BYOD devices effectively:
✑ A. Cloud IAM to enforce token-based MFA: Enhances authentication security but
does not control device compliance.
✑ D. PAM to enforce local password policies: Focuses on privileged account management, not BYOD control.
✑ E. SD-WAN to enforce web content filtering: Enhances network performance and security but does not enforce BYOD device compliance.
✑ F. DLP to enforce data protection capabilities: Protects data but does not control BYOD device access and compliance.
References:
✑ CompTIA SecurityX Study Guide
✑ "Conditional Access Policies," Microsoft Documentation
✑ "Network Access Control (NAC)," Cisco Documentation
A news organization wants to implement workflows that allow users to request that untruthful data be retraced and scrubbed from online publications to comply with the right to be forgotten Which of the following regulations is the organization most likely trying to address'
Correct Answer:
A
The General Data Protection Regulation (GDPR) is the regulation most likely being addressed by the news organization. GDPR includes provisions for the "right to be forgotten," which allows individuals to request the deletion of personal data that is no longer necessary for the purposes for which it was collected. This regulation aims to protect the privacy and personal data of individuals within the European Union.
References:
✑ CompTIA SecurityX Study Guide: Covers GDPR and its requirements, including the right to be forgotten.
✑ GDPR official documentation: Details the rights of individuals, including data erasure and the right to be forgotten.
✑ "GDPR: A Practical Guide to the General Data Protection Regulation" by IT Governance Privacy Team: Provides a comprehensive overview of GDPR compliance, including workflows for data deletion requests.
Users are willing passwords on paper because of the number of passwords needed in an environment. Which of the following solutions is the best way to manage this situation and decrease risks?
Correct Answer:
B
Implementing a Single Sign-On (SSO) solution and integrating it with applications is the best way to manage the situation and decrease risks. Here??s why:
✑ Reduced Password Fatigue: SSO allows users to log in once and gain access to multiple applications and systems without needing to remember and manage multiple passwords. This reduces the likelihood of users writing down passwords.
✑ Improved Security: By reducing the number of passwords users need to manage, SSO decreases the attack surface and potential for password-related security breaches. It also allows for the implementation of stronger authentication methods.
✑ User Convenience: SSO improves the user experience by simplifying the login process, which can lead to higher productivity and satisfaction.
✑ References:
The identity and access management team is sending logs to the SIEM for continuous monitoring. The deployed log collector is forwarding logs to the SIEM. However, only false positive alerts are being generated. Which of the following is the most likely reason for the inaccurate alerts?
Correct Answer:
C
Proper parsing of data is crucial for the SIEM to accurately interpret and analyze the logs being forwarded by the log collector. If the data is not parsed correctly, the SIEM may misinterpret the logs, leading to false positives and inaccurate alerts. Ensuring that the log data is correctly parsed allows the SIEM to correlate and analyze the logs effectively, which is essential for accurate alerting and monitoring.
A security administrator needs to automate alerting. The server generates structured log files that need to be parsed to determine whether an alarm has been triggered Given the following code function: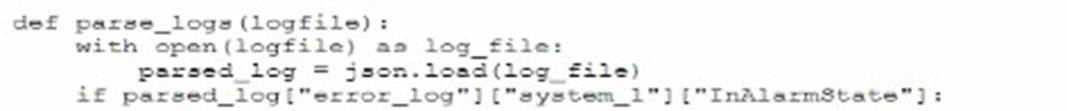
Which of the following is most likely the log input that the code will parse?
A)
B)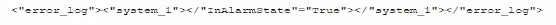
C)
D)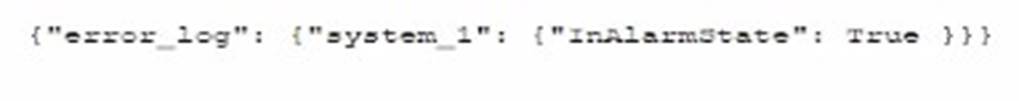
Correct Answer:
A
The code function provided in the question seems to be designed to parse JSON formatted logs to check for an alarm state. Option A is a JSON format that matches the structure likely expected by the code. The presence of the "error_log" and "InAlarmState" keys suggests that this is the correct input format.
Reference: CompTIA SecurityX Study Guide, Chapter on Log Management and Automation, Section on Parsing Structured Logs.

