Your R77 primary Security Management Server is installed on GAiA. You plan to schedule the Security Management Server to run fw logswitch automatically every 48 hours.
How do you create this schedule?
Correct Answer:
B
Study the Rule base and Client Authentication Action properties screen -
After being authenticated by the Security Gateway, when a user starts an HTTP connection to a Web site, the user tries to FTP to another site using the command line. What happens to the user?
Correct Answer:
C
Manual Users must use either telnet to port 259 on the firewall, or use a Web browser to connect to port 900 on the firewall to authenticate before being granted access.
# Partially Automatic If user authentication is configured for the service the user is attempting to access and they pass this authentication, then no further client authentication is required. For example, if HTTP is permitted on a client authentication rule, the user will be able to transparently authenticate since FireWall-1 has a security server for HTTP.Then, if
this setting is chosen, users will not have to manually authenticate for this connection. Note that this applies to all services for which FireWall-1 has built-in security servers (HTTP, FTP, telnet, and rlogin).
# Fully Automatic If the client has the session authentication agent installed, then no further client authentication is required (see session
authentication below). For HTTP, FTP, telnet, or rlogin, the firewall will authenticate via user authentication, and then session authentication will be used to authenticate all other services.
http://www.syngress.com
Figure 6.19 Client Authentication Action Properties 278 Chapter 6 • Authenticating Users
# Agent Automatic Sign On Uses session authentication agent to provide transparent authentication (see session authentication below).
# Single Sign-On System Used in conjunction with UserAuthority servers to provide enhanced application level security. Discussion of UserAuthority is beyond the scope of this book.
Review the rules.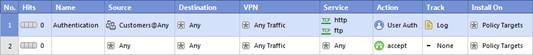
Assume domain UDP is enabled in the impled rules.
What happens when a user from the internal network tries to browse to the internet using HTTP? The user:
Correct Answer:
D
Which of the following items should be configured for the Security Management Server to authenticate via LDAP?
Correct Answer:
B
You want to establish a VPN, using certificates. Your VPN will exchange certificates with an external partner. Which of the following activities should you do first?
Correct Answer:
B

